In addition to the "Maps" that comes pre-installed on the phone, another good app is "Mapquest". Other then showing maps and giving driving directions, this app also provides live traffic reports. Here's a link to the Android Market page or you can search for "Mapquest" in Market from your phone :https://market.android.com/details?id=com.mapquest.android.ace&feature=search_result#?t=W251bGwsMSwxLDEsImNvbS5tYXBxdWVzdC5hbmRyb2lkLmFjZSJd.
In addition to the "Maps" that comes pre-installed on the phone, another good app is "Mapquest". Other then showing maps and giving driving directions, this app also provides live traffic reports. Here's a link to the Android Market page or you can search for "Mapquest" in Market from your phone :https://market.android.com/details?id=com.mapquest.android.ace&feature=search_result#?t=W251bGwsMSwxLDEsImNvbS5tYXBxdWVzdC5hbmRyb2lkLmFjZSJd.Monday, November 7, 2011
Map and directions app
 In addition to the "Maps" that comes pre-installed on the phone, another good app is "Mapquest". Other then showing maps and giving driving directions, this app also provides live traffic reports. Here's a link to the Android Market page or you can search for "Mapquest" in Market from your phone :https://market.android.com/details?id=com.mapquest.android.ace&feature=search_result#?t=W251bGwsMSwxLDEsImNvbS5tYXBxdWVzdC5hbmRyb2lkLmFjZSJd.
In addition to the "Maps" that comes pre-installed on the phone, another good app is "Mapquest". Other then showing maps and giving driving directions, this app also provides live traffic reports. Here's a link to the Android Market page or you can search for "Mapquest" in Market from your phone :https://market.android.com/details?id=com.mapquest.android.ace&feature=search_result#?t=W251bGwsMSwxLDEsImNvbS5tYXBxdWVzdC5hbmRyb2lkLmFjZSJd.Thursday, October 27, 2011
antilvl 1.4.0
it's been a while, but antilvl 1.4.0 is finally released. i did not plan to make another release, but there were some show-stopping bugs in the linux version and some other things that were just embarrassing. :D
major changes include:
you can read more / download here: http://androidcracking.blogspot.com/p/antilvl_01.html
major changes include:
- option to use your own signatures
- more control over which fingerprints are used
- support for verizon drm
- a few new anti-tampering checks are known
- some fixes in how fingerprints were applied
you can read more / download here: http://androidcracking.blogspot.com/p/antilvl_01.html
Monday, October 17, 2011
protection using checksums and key / unlocker apps
if an app requires an unlocker key app, it's likely there will be protection hidden in the key. perhaps the key performs a checksum on the main app, or the key stores pre-computed checksum values for the main app. this is easy to add if you're a developer and is somewhat tricky to handle as a cracker. the reason is the cracker must know how to calculate the checksums himself and inject those values into the app.
calculating checksums is a way to determine if your apk has been modified. there are at least four easy methods to do this. they are: md5, sha1, crc32 and adler32. once you run these guys on your apk you will have either a long number or a byte array. of course, you can't store the checksum in your main app since you wont know the checksum until the app is finished. for this reason, either the calculations or just the checksum values must be stored in another app signed by the same certificate, such as a key / unlocker app.
here's some example code of what the protection may look like in java:
and here's what the above java looks like in smali, so you have some idea what to look for. cracking this will require you to write an app that simulates how the app calculates the checksum. then you'll have to come up with a clever way to get the value into the smali. if it's a long number, this is fairly easy, but if it's a byte array, you may need to use base64 encoding or some other method to make a byte array safe for literal strings. the keywords to look for, of course, are md5, sha1, crc32 and adler32. they may not appear at all if the developer is using reflection to make the method calls.
calculating checksums is a way to determine if your apk has been modified. there are at least four easy methods to do this. they are: md5, sha1, crc32 and adler32. once you run these guys on your apk you will have either a long number or a byte array. of course, you can't store the checksum in your main app since you wont know the checksum until the app is finished. for this reason, either the calculations or just the checksum values must be stored in another app signed by the same certificate, such as a key / unlocker app.
here's some example code of what the protection may look like in java:
// Copied directly and made private from R.java of Key App
// After creating strings..
private static final int tt_crc32=0x7f040002;
private static final int tt_md5=0x7f040004;
public static TestResult checkCRC32ChkSum() {
// Get path to our apk on the system.
String apkPath = Main.MyContext.getPackageCodePath();
Long chksum = null;
try {
// Open the file and build a CRC32 checksum.
// You could also use Adler32 in place of CRC32.
FileInputStream fis = new FileInputStream(new File(apkPath));
CRC32 chk = new CRC32();
CheckedInputStream cis = new CheckedInputStream(fis, chk);
byte[] buff = new byte[80];
while ( cis.read(buff) >= 0 ) ;
chksum = chk.getValue();
} catch (Exception e) {
e.printStackTrace();
}
// After creating your apk, calculate the crc32 checksum
// and store it as a string value in the KEY / unlock App.
String keyStrVal = getKeyString(tt_crc32);
// Key is not installed.
if ( keyStrVal.equals("") ) {
// Key not installed. Validation failure.
}
Long chksumCmp = Long.parseLong(keyStrVal);
if ( chksum.equals(chksumCmp) ) {
// Success. Checksum stored in key matches the
// checksum we just created. We can assume APK
// is not modified. Kinda.
}
else {
// Validation failure! Apk has been modified.
}
}
public static TestResult checkMD5ChkSum() {
// Do pretty much the exact same thing here,
// except instead of a CRC32 checksum, we'll be
// using an MD5 digest. You could also use SHA1.
// Any cracker worth his salt will immediately recognize
// CRC32 and MD5 keywords and know them to be checksum
// attempts. Using Adler32 or SHA1 may put them off.
String apkPath = Main.MyContext.getPackageCodePath();
MessageDigest msgDigest = null;
byte[] digest = null;
try {
msgDigest = MessageDigest.getInstance("MD5");
} catch (NoSuchAlgorithmException e1) {
e1.printStackTrace();
}
byte[] bytes = new byte[8192];
int byteCount;
FileInputStream fis = null;
try {
fis = new FileInputStream(new File(apkPath));
while ((byteCount = fis.read(bytes)) > 0)
msgDigest.update(bytes, 0, byteCount);
digest = msgDigest.digest();
} catch (Exception e) {
e.printStackTrace();
}
String keyStrVal = getKeyString(tt_md5);
// Key is not installed.
if ( keyStrVal.equals("") ) {
// Key not installed. Validation failure.
}
// Using Base64 encoding is just a lazy way to store byte arrays.
// You -could- also embed the values in the code of the Apk
// Read more here:
// http://stackoverflow.com/questions/2721386/android-how-to-share-code-between-projects-signed-with-the-same-certificate
if ( Arrays.equals(Base64.decode(keyStrVal, Base64.DEFAULT), digest) )
// Validated
else
// Apk has been modified
}
private static String getKeyString(int resId) {
// You will need this to retrieve the stored checksums from the KEY App.
String result = "";
try {
Context c = Main.MyContext.createPackageContext("your.package.name.key", Context.CONTEXT_IGNORE_SECURITY);
result = c.getString(resId);
} catch (Exception e) {
Console.log("Error while getting key string:\n" + e);
e.printStackTrace();
result = "";
}
return result;
}
and here's what the above java looks like in smali, so you have some idea what to look for. cracking this will require you to write an app that simulates how the app calculates the checksum. then you'll have to come up with a clever way to get the value into the smali. if it's a long number, this is fairly easy, but if it's a byte array, you may need to use base64 encoding or some other method to make a byte array safe for literal strings. the keywords to look for, of course, are md5, sha1, crc32 and adler32. they may not appear at all if the developer is using reflection to make the method calls.
.method public static checkCRC32ChkSum()V
.locals 11
.prologue
.line 934
sget-object v9, Lcom/lohan/testtarget/Main;->MyContext:Landroid/content/Context;
invoke-virtual {v9}, Landroid/content/Context;->getPackageCodePath()Ljava/lang/String;
move-result-object v0
.line 935
.local v0, apkPath:Ljava/lang/String;
const/4 v3, 0x0
.line 939
.local v3, chksum:Ljava/lang/Long;
:try_start_0
new-instance v7, Ljava/io/FileInputStream;
new-instance v9, Ljava/io/File;
invoke-direct {v9, v0}, Ljava/io/File;->(Ljava/lang/String;)V
invoke-direct {v7, v9}, Ljava/io/FileInputStream;->(Ljava/io/File;)V
.line 940
.local v7, fis:Ljava/io/FileInputStream;
new-instance v2, Ljava/util/zip/CRC32;
invoke-direct {v2}, Ljava/util/zip/CRC32;->()V
.line 942
.local v2, chk:Ljava/util/zip/CRC32;
new-instance v5, Ljava/util/zip/CheckedInputStream;
invoke-direct {v5, v7, v2}, Ljava/util/zip/CheckedInputStream;->(Ljava/io/InputStream;Ljava/util/zip/Checksum;)V
.line 943
.local v5, cis:Ljava/util/zip/CheckedInputStream;
const/16 v9, 0x50
new-array v1, v9, [B
.line 944
.local v1, buff:[B
:cond_0
invoke-virtual {v5, v1}, Ljava/util/zip/CheckedInputStream;->read([B)I
move-result v9
if-gez v9, :cond_0
.line 946
invoke-virtual {v2}, Ljava/util/zip/CRC32;->getValue()J
move-result-wide v9
invoke-static {v9, v10}, Ljava/lang/Long;->valueOf(J)Ljava/lang/Long;
:try_end_0
.catch Ljava/lang/Exception; {:try_start_0 .. :try_end_0} :catch_0
move-result-object v3
.line 953
.end local v1 #buff:[B
.end local v2 #chk:Ljava/util/zip/CRC32;
.end local v5 #cis:Ljava/util/zip/CheckedInputStream;
.end local v7 #fis:Ljava/io/FileInputStream;
:goto_0
const v9, 0x7f040002
invoke-static {v9}, Lcom/lohan/testtarget/PerformTestsTask;->getKeyString(I)Ljava/lang/String;
move-result-object v8
.line 956
.local v8, keyStrVal:Ljava/lang/String;
const-string v9, ""
invoke-virtual {v8, v9}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
.line 960
invoke-static {v8}, Ljava/lang/Long;->parseLong(Ljava/lang/String;)J
move-result-wide v9
invoke-static {v9, v10}, Ljava/lang/Long;->valueOf(J)Ljava/lang/Long;
move-result-object v4
.line 962
.local v4, chksumCmp:Ljava/lang/Long;
invoke-virtual {v3, v4}, Ljava/lang/Long;->equals(Ljava/lang/Object;)Z
.line 970
return-void
.line 947
.end local v4 #chksumCmp:Ljava/lang/Long;
.end local v8 #keyStrVal:Ljava/lang/String;
:catch_0
move-exception v9
move-object v6, v9
.line 948
.local v6, e:Ljava/lang/Exception;
invoke-virtual {v6}, Ljava/lang/Exception;->printStackTrace()V
goto :goto_0
.end method
.method public static checkMD5ChkSum()V
.locals 12
.prologue
const/4 v11, 0x0
.line 981
sget-object v10, Lcom/lohan/testtarget/Main;->MyContext:Landroid/content/Context;
invoke-virtual {v10}, Landroid/content/Context;->getPackageCodePath()Ljava/lang/String;
move-result-object v0
.line 982
.local v0, apkPath:Ljava/lang/String;
const/4 v9, 0x0
.line 983
.local v9, msgDigest:Ljava/security/MessageDigest;
const/4 v3, 0x0
check-cast v3, [B
.line 985
.local v3, digest:[B
:try_start_0
const-string v10, "MD5"
invoke-static {v10}, Ljava/security/MessageDigest;->getInstance(Ljava/lang/String;)Ljava/security/MessageDigest;
:try_end_0
.catch Ljava/security/NoSuchAlgorithmException; {:try_start_0 .. :try_end_0} :catch_0
move-result-object v9
.line 990
:goto_0
const/16 v10, 0x2000
new-array v2, v10, [B
.line 992
.local v2, bytes:[B
const/4 v6, 0x0
.line 995
.local v6, fis:Ljava/io/FileInputStream;
:try_start_1
new-instance v7, Ljava/io/FileInputStream;
new-instance v10, Ljava/io/File;
invoke-direct {v10, v0}, Ljava/io/File;->(Ljava/lang/String;)V
invoke-direct {v7, v10}, Ljava/io/FileInputStream;->(Ljava/io/File;)V
:try_end_1
.catch Ljava/lang/Exception; {:try_start_1 .. :try_end_1} :catch_2
.line 997
.end local v6 #fis:Ljava/io/FileInputStream;
.local v7, fis:Ljava/io/FileInputStream;
:goto_1
:try_start_2
invoke-virtual {v7, v2}, Ljava/io/FileInputStream;->read([B)I
move-result v1
.local v1, byteCount:I
if-gtz v1, :cond_0
.line 1000
invoke-virtual {v9}, Ljava/security/MessageDigest;->digest()[B
:try_end_2
.catch Ljava/lang/Exception; {:try_start_2 .. :try_end_2} :catch_1
move-result-object v3
move-object v6, v7
.line 1005
.end local v1 #byteCount:I
.end local v7 #fis:Ljava/io/FileInputStream;
.restart local v6 #fis:Ljava/io/FileInputStream;
:goto_2
const v10, 0x7f040004
invoke-static {v10}, Lcom/lohan/testtarget/PerformTestsTask;->getKeyString(I)Ljava/lang/String;
move-result-object v8
.line 1007
.local v8, keyStrVal:Ljava/lang/String;
const-string v10, ""
invoke-virtual {v8, v10}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
.line 1015
invoke-static {v8, v11}, Landroid/util/Base64;->decode(Ljava/lang/String;I)[B
move-result-object v10
invoke-static {v10, v3}, Ljava/util/Arrays;->equals([B[B)Z
.line 1020
return-void
.line 986
.end local v2 #bytes:[B
.end local v6 #fis:Ljava/io/FileInputStream;
.end local v8 #keyStrVal:Ljava/lang/String;
:catch_0
move-exception v10
move-object v5, v10
.line 987
.local v5, e1:Ljava/security/NoSuchAlgorithmException;
invoke-virtual {v5}, Ljava/security/NoSuchAlgorithmException;->printStackTrace()V
goto :goto_0
.line 998
.end local v5 #e1:Ljava/security/NoSuchAlgorithmException;
.restart local v1 #byteCount:I
.restart local v2 #bytes:[B
.restart local v7 #fis:Ljava/io/FileInputStream;
:cond_0
const/4 v10, 0x0
:try_start_3
invoke-virtual {v9, v2, v10, v1}, Ljava/security/MessageDigest;->update([BII)V
:try_end_3
.catch Ljava/lang/Exception; {:try_start_3 .. :try_end_3} :catch_1
goto :goto_1
.line 1001
.end local v1 #byteCount:I
:catch_1
move-exception v10
move-object v4, v10
move-object v6, v7
.line 1002
.end local v7 #fis:Ljava/io/FileInputStream;
.local v4, e:Ljava/lang/Exception;
.restart local v6 #fis:Ljava/io/FileInputStream;
:goto_3
invoke-virtual {v4}, Ljava/lang/Exception;->printStackTrace()V
goto :goto_2
.line 1001
.end local v4 #e:Ljava/lang/Exception;
:catch_2
move-exception v10
move-object v4, v10
goto :goto_3
.end method
.method private static asdfgetKeyString(I)Ljava/lang/String;
.locals 6
.parameter "resId"
.prologue
.line 1025
const-string v2, ""
.line 1028
.local v2, result:Ljava/lang/String;
:try_start_0
sget-object v3, Lcom/lohan/testtarget/Main;->MyContext:Landroid/content/Context;
const-string v4, "your.package.name.key"
const/4 v5, 0x2
invoke-virtual {v3, v4, v5}, Landroid/content/Context;->createPackageContext(Ljava/lang/String;I)Landroid/content/Context;
move-result-object v0
.line 1029
.local v0, c:Landroid/content/Context;
invoke-virtual {v0, p0}, Landroid/content/Context;->getString(I)Ljava/lang/String;
:try_end_0
.catch Ljava/lang/Exception; {:try_start_0 .. :try_end_0} :catch_0
move-result-object v2
.line 1036
.end local v0 #c:Landroid/content/Context;
:goto_0
return-object v2
.line 1030
:catch_0
move-exception v3
move-object v1, v3
.line 1031
.local v1, e:Ljava/lang/Exception;
new-instance v3, Ljava/lang/StringBuilder;
const-string v4, "Error while getting key string:\n"
invoke-direct {v3, v4}, Ljava/lang/StringBuilder;->(Ljava/lang/String;)V
invoke-virtual {v3, v1}, Ljava/lang/StringBuilder;->append(Ljava/lang/Object;)Ljava/lang/StringBuilder;
move-result-object v3
invoke-virtual {v3}, Ljava/lang/StringBuilder;->toString()Ljava/lang/String;
move-result-object v3
invoke-static {v3}, Lcom/lohan/testtarget/Console;->log(Ljava/lang/String;)V
.line 1032
invoke-virtual {v1}, Ljava/lang/Exception;->printStackTrace()V
.line 1033
const-string v2, ""
goto :goto_0
.end method
Wednesday, August 10, 2011
Cost-it
1. Create a Project
2. Edit Project Details
3. Open a Project
4. Delete a Project
5. Add a Task
6. Edit a Task Details
7. Complete a Task
8. Delete a Task
9. View Reports
Cost-It is a small, intuitive and easy-to-use application. The basic idea is that you define a project (and optional budget), its tasks and associated costs (estimated, actual, and how much you have paid). You then know how much the project is estimated to cost you; how much the project has actually cost you; and how much you have paid and have left to pay.
If you planning on getting married, have some DIY projects to cost out and track; or are planning your latest vacation then this is the application for you.
You can also check tasks off as done so you know the completion status of each project in terms of tasks complete and how much money has been spent and still needs to be spent.
This application is ideal for Wedding planning, DIY Projects, Vacation Planning. No Project is too big or small.
0. Configuring Cost-It
You can configure this application to use up to three additional custom attributes for a task.
You can configure this application to use up to three additional custom attributes for a task.
From the main projects screen select the menu button.
This will load the Preferences page. From here you can enable up to three attributes and give them a name.
This feature is useful if you have custom values you want to track such as tax, shipping or resale value.
This feature is only available from version 1.3.
This feature is only available from version 1.3.
1. Creating a Project
To create your first Project, tap on the add icon at the top right of the screen. This will open up the Edit Project dialog as shown below:
Within this dialog you can enter the name of the project and the size of the budget (if required)
To confirm you want to create the project tap on the OK button. This will take you to the task management screen where you can add, edit and delete tasks from within your project.
To go back to the projects screen tap on the back button.
Within this dialog you can enter the name of the project and the size of the budget (if required)
To confirm you want to create the project tap on the OK button. This will take you to the task management screen where you can add, edit and delete tasks from within your project.
To go back to the projects screen tap on the back button.
2. Edit Project Details
To edit the project, from the projects screen tap on the project and a quick action bar will appear as shown below:
Tap on the Edit Project option, this will open Edit Project Dialog where the details can be modified.
You can also edit the project details from the tasks page, by selecting the edit icon to the right of the project name.
3. Open a Project
To open the project and edit the projects tasks, you tap on the project so the Quick Action Bar appears. You then Tap on Edit Tasks option.
Alternatively you can swipe across project, from left-to-right or right-to-left.
This will open the page to edit tasks.
4. Delete a Project
To delete a project you tap on the project to open up the Quick Action Bar.
You then tap on the Delete option.
A confirmation dialog box will appear to ask if this is what you really want to do. Select either OK or Cancel.
5. Add a Task
6. Edit a Task
To edit the task, from the tasks screen tap on the Task and a quick action bar will appear as shown below:
Tap on the Edit option, this will open Edit Task Dialog where the details can be modified.
To edit the project, from the projects screen tap on the project and a quick action bar will appear as shown below:
Tap on the Edit Project option, this will open Edit Project Dialog where the details can be modified.
You can also edit the project details from the tasks page, by selecting the edit icon to the right of the project name.
3. Open a Project
To open the project and edit the projects tasks, you tap on the project so the Quick Action Bar appears. You then Tap on Edit Tasks option.
Alternatively you can swipe across project, from left-to-right or right-to-left.
This will open the page to edit tasks.
4. Delete a Project
To delete a project you tap on the project to open up the Quick Action Bar.
You then tap on the Delete option.
A confirmation dialog box will appear to ask if this is what you really want to do. Select either OK or Cancel.
5. Add a Task
To create a Task, tap on the add icon at the top right of the screen. This will open up the Edit Task dialog as shown below:
Within this dialog you can enter the name of the task, the estimated cost, the actual cost; and how much you have paid so far.
Tap on the OK button to save this information.
Within this dialog you can enter the name of the task, the estimated cost, the actual cost; and how much you have paid so far.
Tap on the OK button to save this information.
6. Edit a Task
To edit the task, from the tasks screen tap on the Task and a quick action bar will appear as shown below:
Tap on the Edit option, this will open Edit Task Dialog where the details can be modified.
7. Complete a Task
You have two options for checking/unchecking a task.
1) Select Check from the Quick Action Bar
2) Swipe over the Task from left-to-right or right-to-left.
You have two options for checking/unchecking a task.
1) Select Check from the Quick Action Bar
2) Swipe over the Task from left-to-right or right-to-left.
8. Delete a Task
To delete a Task you tap on the Task to open up the Quick Action Bar.
You then tap on the Delete option.
A confirmation dialog box will appear to ask if this is what you really want to do. Select either OK or Cancel.
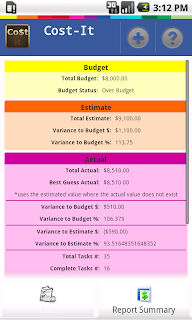
9. View Reports
To view reports for this project you select the Report Summary Tab at the bottom of the tasks screen.
The following screen will appear:
If you like this application then please give us a good rating.
Friday, June 10, 2011
cracking verizon's v cast apps drm
verizon has a new app store. it has an amazon-store like drm that's fairly simple to crack.
here's how it works. in the launching activity a thread is started that calls checkLicense(). this was in com/cp/app/MainActivity$2.smali:
if you look at isDRMDone() you'll see that it's basically a big switch. input of 0 or 1 counts as valid. everything else is some kind of error. so we just need to make sure checkLicense returns 1 and doesn't call anything else that may have side effects (timeouts, checking to see if verizon app store is installed, etc..).
checkLicense() is defined in com/verizon/vcast/apps/LicenseAuthenticator.smali. after modification it looks like:
if you're a developer, depending on how they implement the insertion of their drm, it may still be possible to use classical protection / anti-tampering techniques. i'd like to know. but really though, don't waste your time on protection. i'm not blasting verizon or amazon or google for weak security. real effort should be spent improving the program, not slowing down (because you can't stop) crackers. if you want money, use ads.
here's how it works. in the launching activity a thread is started that calls checkLicense(). this was in com/cp/app/MainActivity$2.smali:
.method public run()V
.locals 2
.prologue
.line 100
invoke-static {}, Landroid/os/Looper;->prepare()V
.line 102
:try_start_0
iget-object v0, p0, Lcom/cp/app/MainActivity$2;->this$0:Lcom/cp/app/MainActivity;
iget-object v0, v0, Lcom/cp/app/MainActivity;->licenseAuthenticator:Lcom/verizon/vcast/apps/LicenseAuthenticator;
sget-object v1, Lcom/cp/app/MainActivity;->verizonAppKeyword:Ljava/lang/String;
# call checkLicense and store result in v0
invoke-virtual {v0, v1}, Lcom/verizon/vcast/apps/LicenseAuthenticator;->checkLicense(Ljava/lang/String;)I
move-result v0
.line 103
iget-object v1, p0, Lcom/cp/app/MainActivity$2;->this$0:Lcom/cp/app/MainActivity;
# send result of checkLicense (v0) to isDRMDone()
invoke-virtual {v1, v0}, Lcom/cp/app/MainActivity;->isDRMDone(I)Z
move-result v0
# isDRMDone() handles error messages and returns true when all is good
if-eqz v0, :cond_0
# ... rest of code
if you look at isDRMDone() you'll see that it's basically a big switch. input of 0 or 1 counts as valid. everything else is some kind of error. so we just need to make sure checkLicense returns 1 and doesn't call anything else that may have side effects (timeouts, checking to see if verizon app store is installed, etc..).
checkLicense() is defined in com/verizon/vcast/apps/LicenseAuthenticator.smali. after modification it looks like:
.method public declared-synchronized checkLicense(Ljava/lang/String;)I
.locals 10
.parameter "keyword"
.prologue
# just set v0 to true and return
# the rest of the code never runs
const/4 v0, 0x1
return v0
const/16 v9, 0x64
const-string v7, "checkLicense() finished. Trying to shutDownLicenseService()"
const-string v7, "LicenseAuthenticator"
.line 256
monitor-enter p0
:try_start_0
const-string v7, "LicenseAuthenticator"
const-string v8, "begin checkLicense()"
# ... rest of code
if you're a developer, depending on how they implement the insertion of their drm, it may still be possible to use classical protection / anti-tampering techniques. i'd like to know. but really though, don't waste your time on protection. i'm not blasting verizon or amazon or google for weak security. real effort should be spent improving the program, not slowing down (because you can't stop) crackers. if you want money, use ads.
Wednesday, June 8, 2011
anti-tampering with crc check
one way an app will try to detect if it has been tampered with is to look at classes.dex inside the apk. just so you know, java code is compiled to java .class files, which is then transformed by dx into classes.dex. this one file contains all the compiled code of an app. once the code is finished and the app is ready to be published, properties of the file such as the size or crc (cyclic redundancy check) can be determined and then stored inside the resources of the app.
when the app runs, it can compare the stored values with the actual values of the classes.dex file. if they do not match, then the code was likely tampered with.
note that we're using zipentry here, but we could also use jarentry and jarfile. you can't simply look for getCrc() and feel safe either, because the method could be called with reflection.
here's what a crc check may look like in java:
and here's the above code translated into smali:
when the app runs, it can compare the stored values with the actual values of the classes.dex file. if they do not match, then the code was likely tampered with.
note that we're using zipentry here, but we could also use jarentry and jarfile. you can't simply look for getCrc() and feel safe either, because the method could be called with reflection.
here's what a crc check may look like in java:
private void crcTest() throws IOException {
boolean modified = false;
// required dex crc value stored as a text string.
// it could be any invisible layout element
long dexCrc = Long.parseLong(Main.MyContext.getString(R.string.dex_crc));
ZipFile zf = new ZipFile(Main.MyContext.getPackageCodePath());
ZipEntry ze = zf.getEntry("classes.dex");
if ( ze.getCrc() != dexCrc ) {
// dex has been modified
modified = true;
}
else {
// dex not tampered with
modified = false;
}
}and here's the above code translated into smali:
.method private crcTest()V
.locals 7
.annotation system Ldalvik/annotation/Throws;
value = {
Ljava/io/IOException;
}
.end annotation
.prologue
.line 599
const/4 v2, 0x0
.line 602
# modified will be set to true if classes.dex crc is not what it should be
.local v2, modified:Z
sget-object v5, Lcom/lohan/testtarget/Main;->MyContext:Landroid/content/Context;
# get the crc value from string resources
const v6, 0x7f040002
invoke-virtual {v5, v6}, Landroid/content/Context;->getString(I)Ljava/lang/String;
move-result-object v5
# convert it to a long since ZipEntry.getCrc gives us long
invoke-static {v5}, Ljava/lang/Long;->parseLong(Ljava/lang/String;)J
move-result-wide v0
.line 604
.local v0, dexCrc:J
new-instance v4, Ljava/util/zip/ZipFile;
sget-object v5, Lcom/lohan/testtarget/Main;->MyContext:Landroid/content/Context;
# get the path to the apk on the system
invoke-virtual {v5}, Landroid/content/Context;->getPackageCodePath()Ljava/lang/String;
move-result-object v5
invoke-direct {v4, v5}, Ljava/util/zip/ZipFile;->(Ljava/lang/String;)V
.line 605
.local v4, zf:Ljava/util/zip/ZipFile;
# get classes.dex entry from our apk
const-string v5, "classes.dex"
invoke-virtual {v4, v5}, Ljava/util/zip/ZipFile;->getEntry(Ljava/lang/String;)Ljava/util/zip/ZipEntry;
move-result-object v3
.line 607
.local v3, ze:Ljava/util/zip/ZipEntry;
# you could crack here by providing v5 with the correct
# long value. this may be easier if later logic is convoluted
# or if the result is stored in a class variable and acted
# on later. you can write your own java program to get the
# correct value.
invoke-virtual {v3}, Ljava/util/zip/ZipEntry;->getCrc()J
move-result-wide v5
# compare v5 (actual crc) with v0 (stored crc)
cmp-long v5, v5, v0
# if v5 is 0, meaning cmp-long reports values are NOT the same
# goto :cond_0. this is where this could be cracked.
# could simply remove this line, in this case.
if-eqz v5, :cond_0
.line 609
# otherwise store true in v2.
# normally there will be code to act on the value of v2.
const/4 v2, 0x1
.line 615
:goto_0
return-void
.line 613
:cond_0
# store false in v2.
const/4 v2, 0x0
goto :goto_0
.end method
Monday, June 6, 2011
protection by checking for debuggers
one way to figure out what an app is doing is to use a debugger so you can step through line by line. apktool makes it possible to debug apps to which you do not have the source, and you also have to setup a few other things covered in lesson 1 of the way of the android crack tutorials.
some apps try to protect against this and there are two techniques of doing so. the first is to check the android manifest to see if the app is set to debuggable. the java code would look something like this:
in smali, specifically from the testtarget app distributed with antilvl, it looks like:
the second method is to check if a debugger is currently connected. the java looks like:
some apps try to protect against this and there are two techniques of doing so. the first is to check the android manifest to see if the app is set to debuggable. the java code would look something like this:
boolean isDebuggable = (0 != (getApplcationInfo().flags &= ApplicationInfo.FLAG_DEBUGGABLE));
if ( isDebuggable )
invalidLicense(); // you get the idea
in smali, specifically from the testtarget app distributed with antilvl, it looks like:
# get app info object
invoke-virtual {p0}, Lcom/lohan/testtarget/Main;->getApplicationInfo()Landroid/content/pm/ApplicationInfo;
move-result-object v1
# get flags mask
iget v2, v1, Landroid/content/pm/ApplicationInfo;->flags:I
# 0x2 is ApplicationInfo.FLAG_DEBUGGABLE
and-int/lit8 v2, v2, 0x2
iput v2, v1, Landroid/content/pm/ApplicationInfo;->flags:I
# if v2 is 0x0 (the debuggable flag is not set), goto :cond_0
if-eqz v2, :cond_0
the second method is to check if a debugger is currently connected. the java looks like:
boolean debugConn = Debug.isDebuggerConnected();
Subscribe to:
Posts (Atom)